A new vulnerability has been identified in the WordPress plugin Easy WP SMTP, right from the daily debug file.
A few days ago, "WP eCommerce" patched the easily exploitable and dangerous vulnerability found by NinTechNet, Easy WP SMTP WordPress plugin Version 1.4.3 has been released.
Easy WP SMTP plugin version 1.4.2 and older versions appear to be vulnerable due to sensitive information disclosure. This plugin is known to have more than 500,000 active users.
Since there are some steps to exploit the vulnerability, it is difficult to determine the actual number of installations affected by the vulnerability.
Security vulnerability: Reset unauthenticated administrator password Corrected: 1.4.3 Number of sites affected: 500.000+
Vulnerability in Easy WP SMTP WordPress Plugin
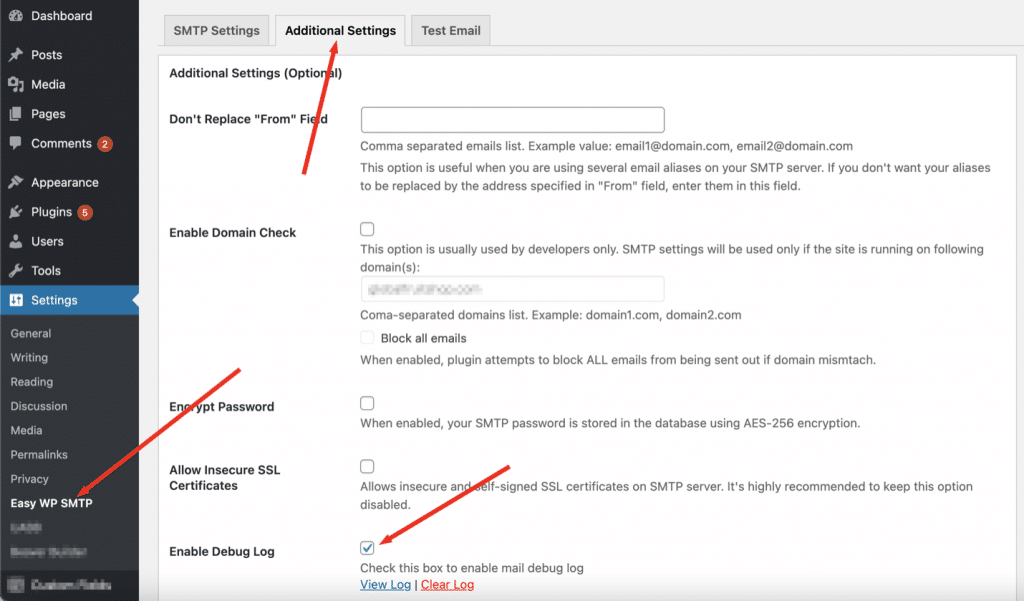
First, let's mention that Easy WP SMTP has a debug logging option. When enabled, this function writes all information about WordPress emails to a .txt file and also hosts the email content in plain text format. The content of these emails is the most important threat in this case.
WordPress sends an email with a temporary custom link when you initiate a password reset, and the link redirects to a password reset form that allows you to set a new password for the account.
This method is safe as long as the mail system is secure and no one but the actual user can receive these emails with password renewal links. This is in contrast to the Easy WP SMTP plugin's does not have the necessary protection for the main directory content appeared .
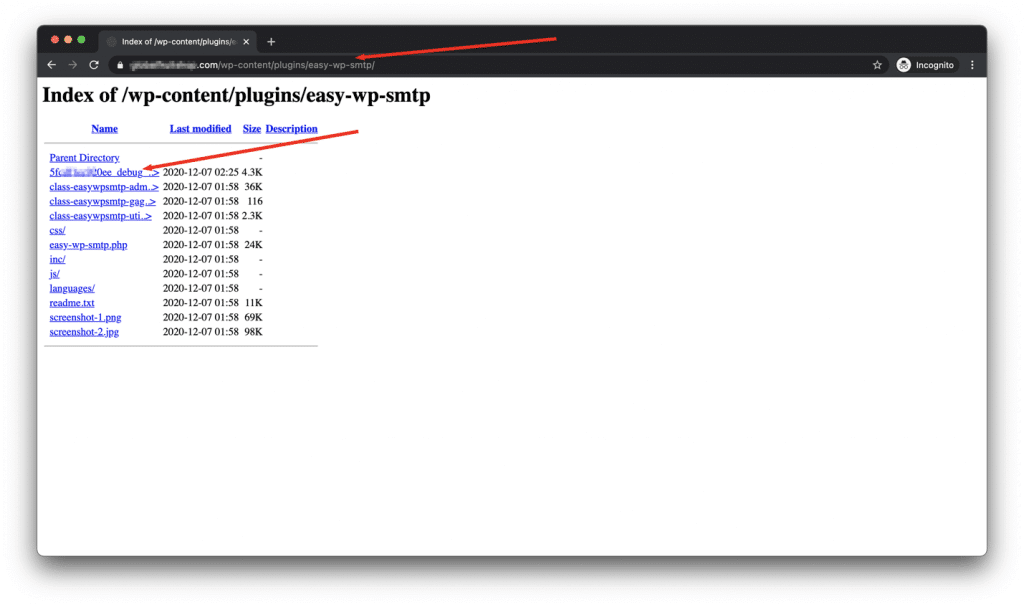
It was noticed that the Easy WP SMTP plugin did not initially contain any index.html or index.php files in its main directory where these log files are stored, thus creating a vulnerability.
For sites hosted on servers with a sufficiently secure configuration and other security measures or tools that prevent directory listing, this vulnerability is closed by itself. However, if the server configuration allows directory listing and there are no other factors in place to prevent it, then it could be compromising your entire system.
In this case, we can see all files and directories, including the log file containing sensitive information.
There are a few steps to exploit this vulnerability: if the logging function is active, the directory is accessible and all that remains is to enumerate or guess the username or email whose password we will try to reset.
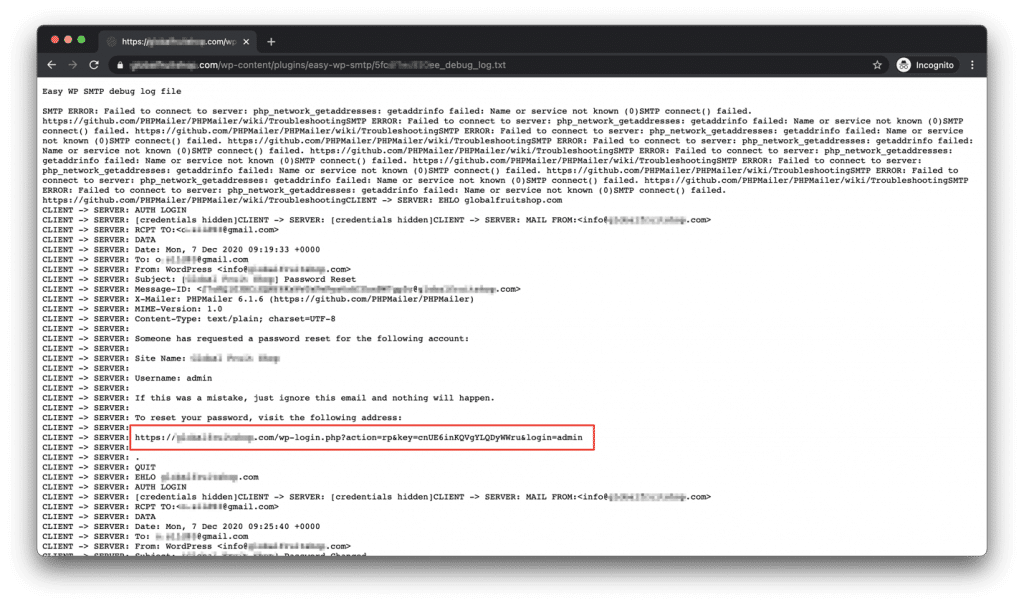
You can now visit the WordPress login form Click on "Lost your password?" The link that will allow us to enter the username or email address of the user whose password we want to reset will appear in the log records.
Immediately afterwards, WordPress will send an email with a password reset link. This is the situation, anyone can read the password reset link and reset password for which he can use the link means . An attacker can reset the password of any user with any privilege. The vulnerability is not limited to a specific username or user role.
As you can see, this vulnerability is easy to exploit. It doesn't require any special knowledge, which makes it even more dangerous.
Solution
You can update the plugin to the latest available version (1.4.3), but if you still want to keep the log function on, I suggest you be careful.
In most cases, the plugin directory may be indexed by Google and possibly other search engines. If the attacker can get the actual log file name from the SERPs, closing the directory listing will not prevent sensitive data leaks.
If an attacker knows the full path to the log files, they can access it directly, even if the directory listing is disabled.
How to disable directory listing on the site?
Directory listing functionality is part of the web server configuration. If you have noticed that your server configuration allows directory listing, but you do not have rights to change the server configuration, you can override some parameters by adding small snippets of code to your .htaccess file.
To disable the directory listing, you must add the following line to your .htaccess file located in the root (main) directory of your website:
Options -Indexes
Timeline
06.12.2020 – https://profiles.wordpress.org/mathieg2/ 07.12.2020 - Plugin received patch 1.4.3 (index.html added to index)