Gurmehub Campaigns Review Now!
POS Integrator PRO Now On Sale! Buy Now
TravelerWP Integration Now at POS Integrator Try Now

The WordPress login URL is the same for every WordPress site and does not require any special permissions for access. Anyone with experience working with WordPress will know that the login URL /wp-login.php knows that it is found on the page.
The accessibility of the WordPress login page makes it the most hacked and possibly the most vulnerable part of any WordPress website. Fortunately for us, the iThemes Security Pro plugin makes it easy to protect your WordPress login details.
Let's take a look at the tools you can use to secure your WordPress login credentials in Themes Security Pro and make them virtually impenetrable!
The first step to securing your WordPress login is to limit failed login attempts. By default, there is no feature that comes with WordPress to limit the number of failed login attempts a person can make. Without a limit on the number of failed login attempts an attacker can make, they can keep trying a combination of different usernames and passwords until they find an account that can log in.
iThemes Security Pro Local Brute Force Protection The feature also keeps a record of invalid login attempts made with a host or IP address and username. When an IP or username makes too many invalid login attempts in a row, they are locked and prevented from making further attempts for a certain period of time.
Local Brute Force Protection feature, enable it on the main page of the iThemes Security settings page to start using it.

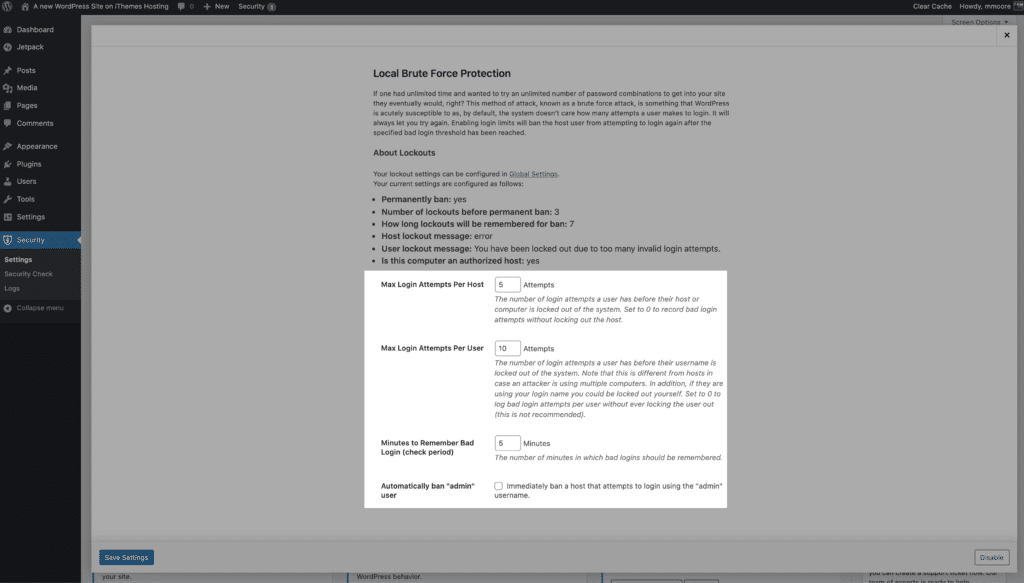
There are a few things to keep in mind when configuring your lockdown settings. Let's say your website is under brute force attack and the attacker is using your username. The goal is to lock out the attacker's IP, not your username, so that even if your website is under attack you can still log in and get things done,
You also don't want to make these settings too strict by setting the number of invalid login attempts too low and the time to remember invalid attempts too long. If you lower the number of invalid login attempts for hosts/IPs to 1 and set the minutes to remember bad login attempt to a month, you greatly increase the likelihood of accidentally locking out legitimate users.
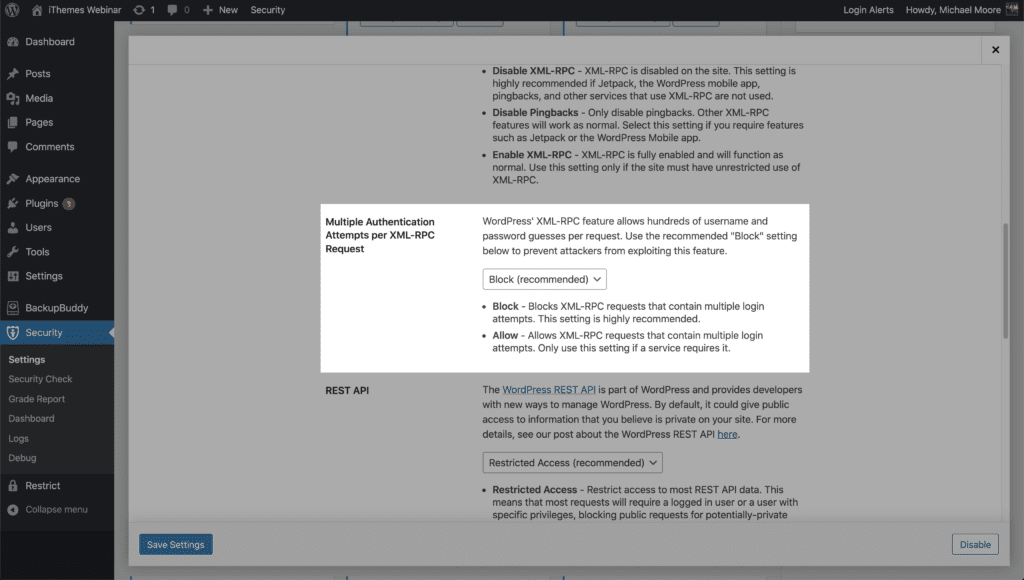
Besides using a login form, there are other ways to log in to WordPress. Using XML-RPC, an attacker can make hundreds of username and password attempts in a single HTTP request. The brute force method allows attackers to make thousands of username and password attempts using XML-RPC in just a few HTTP requests.
Themes Security Pro WordPress Tweaks settings, you can prevent multiple authentication attempts per XML-RPC request. Limiting the number of username and password attempts to one per request is a crucial step in securing your WordPress login
Limiting login attempts is all about brute force protection. Brute force protection only looks at attempts to access your site and bans users based on lockdown rules specified in your security settings.
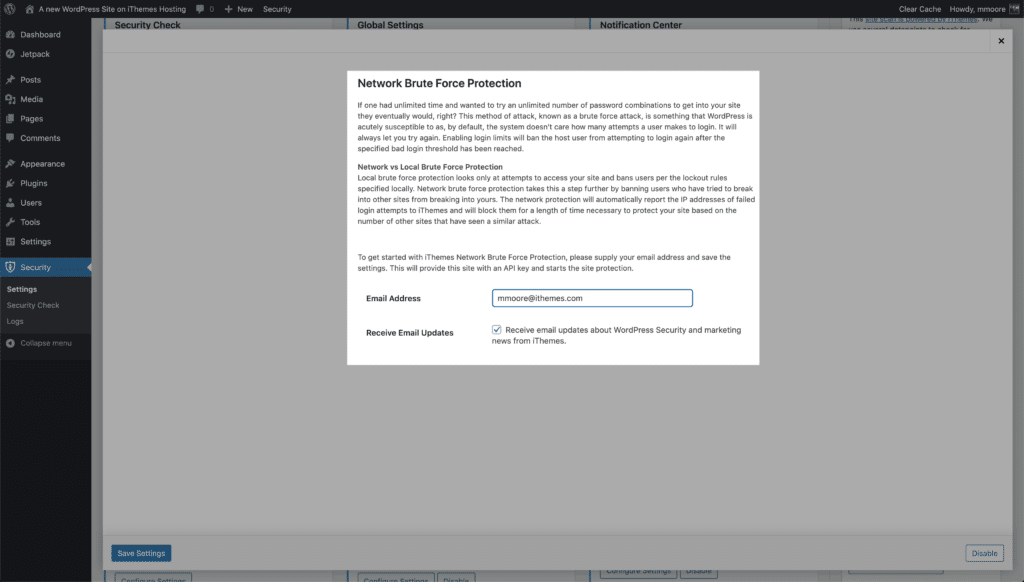
Network Brute Force protection takes this one step further. If it is determined that an IP is trying to enter websites in the iThemes Security community, the IP is added to the Network Bruce Force banned list.
When an IP enters the Network Brute Force banned list, the IP is blocked on all websites on the network. So if an IP attacks my website and gets banned, it will be reported to iThemes Security Brute Force Network. My report can help to get the IP banned on the whole network.
Network Power Protection enable it on the main page of the security settings to start using it.
Then enter your email address, select whether you would like to receive email updates, and then Save Click on the button.
In a list compiled by Splash Data, the most common password found in all data dumps was 123456. Data dump, somewhere on the internet thrown is a hacked database full of user passwords. If the most common password in the data dumps is 123456, can you imagine how many people on your website use a weak password?
Using a weak password is like locking your front door with a piece of tape. Now that hackers are using computer graphics cards in their attacks, the time it takes to crack a password is much shorter.
For example, a high-performance password cracking company Terahash created by the company's team at the time of writing. Their graph shows how long it takes to crack a password using the hashstack set of 448x RTX 2080s.
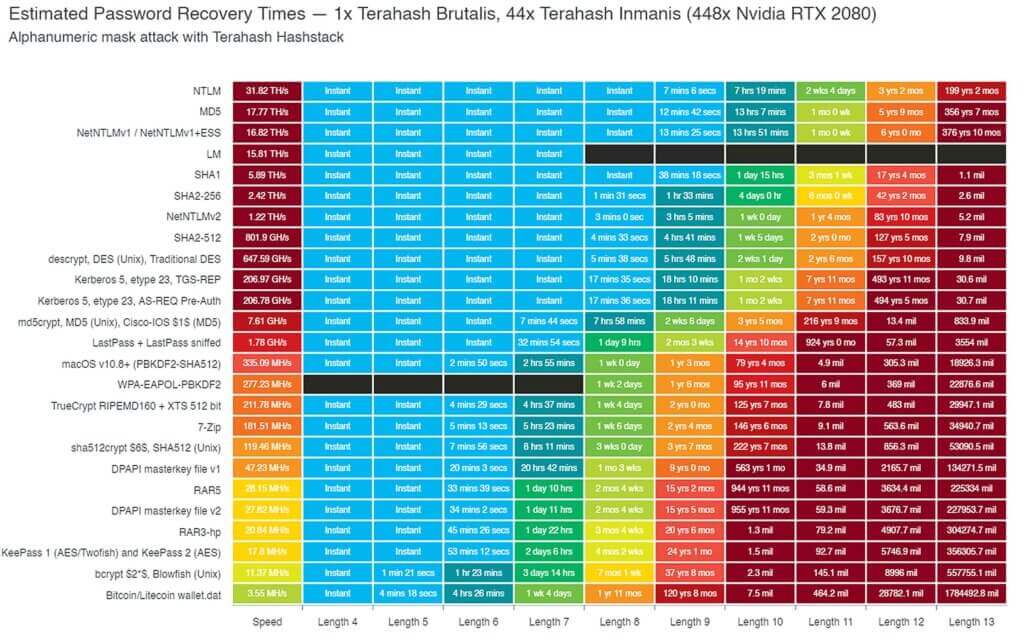
By default WordPress stored in the WP database uses MD5 to hash user passwords . So, according to this table, Terahash can crack an 8-character password almost instantly. This is not only very impressive, but also really scary. The good news is that we can secure our WordPress login by requiring our top users to use strong passwords.
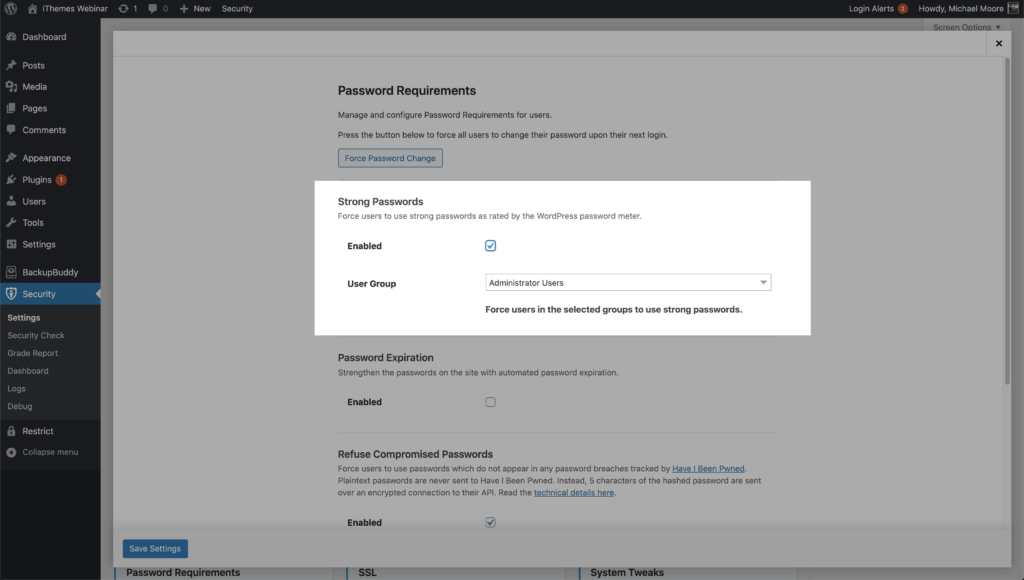
iThemes Security Pro Passwords Requirementi feature allows you to force certain users to use a strong password. On the main page of the security settings Password Requirements and then select the users you want to require to use a strong password.
Verizon Data Penetration Investigations ReportIn , the most important statistic is that hackers exploit stolen or weak passwords in % 81 of breaches.
Hackers use a form of brute force that is attacked and called a dictionary attack. A dictionary attack is a method of breaking into a WordPress website with commonly used passwords seen in database dumps. The Data Breach hosted on MEGA contained 1,160,253,228 unique email address and password combinations.
Preventing users with author-level skills and more from using compromised passwords to protect your WordPress logins is a must. You may also want to consider not allowing your lower-level users to use compromised passwords.
Making it as easy as possible to create a new customer account is completely understandable and encouraged. However, your customer may not know that the password they are using is contained in a data dump. By alerting your customer that the password they are using has been compromised, you are doing them a great service.
On the main page of the security settings Password Requirements and then select the users you want to prevent from using a compromised password.

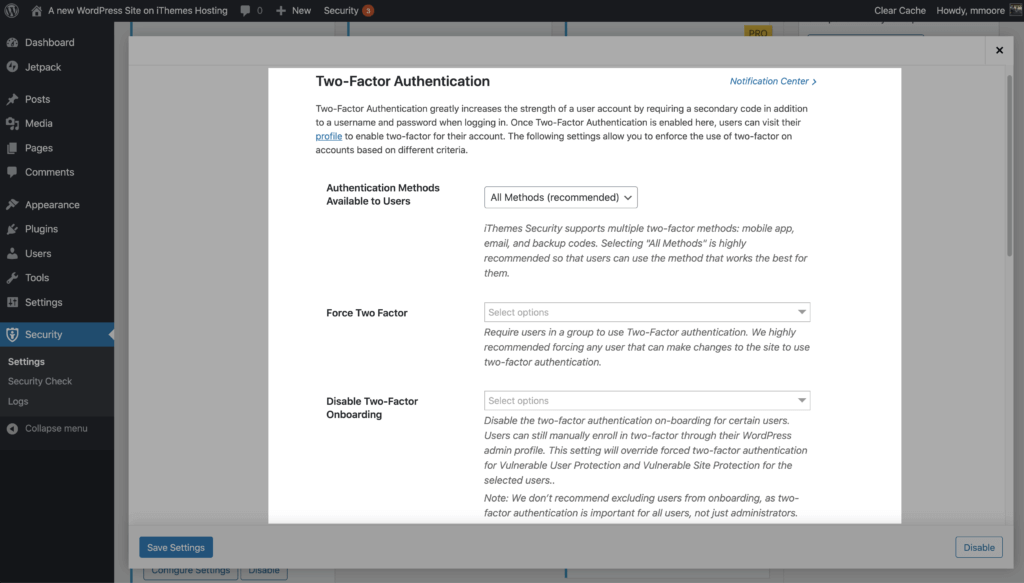
Using two-factor authentications is the best thing you can do to secure your WordPress login. Two-factor authentication is the process of verifying a person's identity by requiring two separate verification methods. Google, on his blog shared that using two-factor authentication can stop automated bot attacks% 100.
Themes Security Pro Two-factor authentication gives your site security flexibility. You can enable two-factor for all or some of your users and force your top users to use 2fa for every login.
Themes Security Pro, Google reCAPTCHA feature protects your site against bad bots. These bots may be trying to break into your website by using compromised passwords, sending spam or even harvesting your content. reCAPTCHA uses advanced risk analysis techniques to distinguish between humans and bots.
The great thing about ReCAPTCHA version 3 is that it helps you detect abusive bot traffic on your website without any user interaction. Instead of showing a CAPTCHA query, ReCAPTCHA v3 tracks the different requests made on your site and returns a score for each request. The score ranges from 0.0 to 1. The higher the score ReCAPTCHA returns, the more confident it is that a human made a request. The lower this score returned by ReCAPTCHA, the more certain it is that a bot is making the request.
Google reCAPTCHA v3 to start using , enable the option on the main page of the security settings.
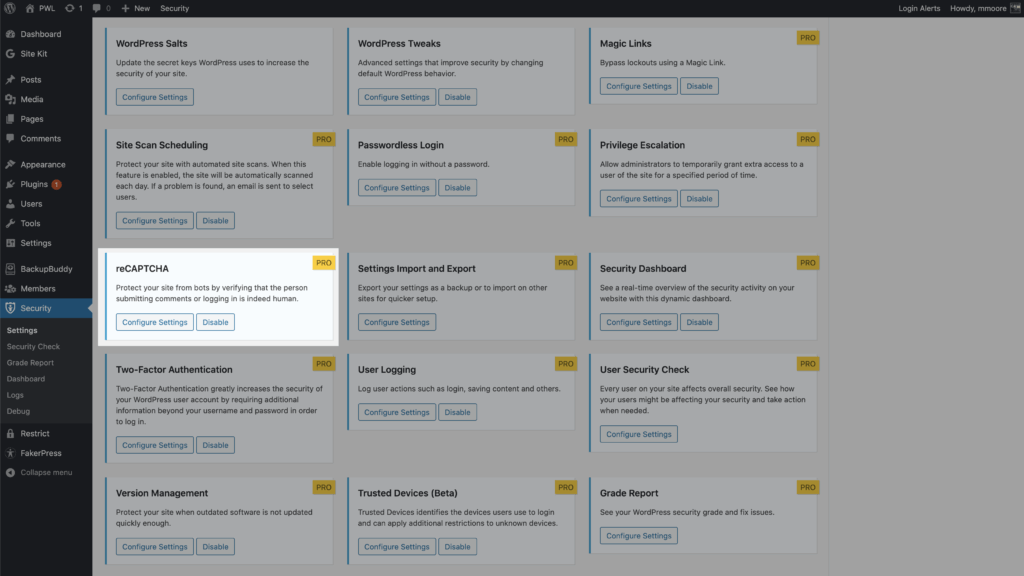
Then, reCAPTCHA you will need to select reCAPTCHA v3 and generate your keys from your Google admin.
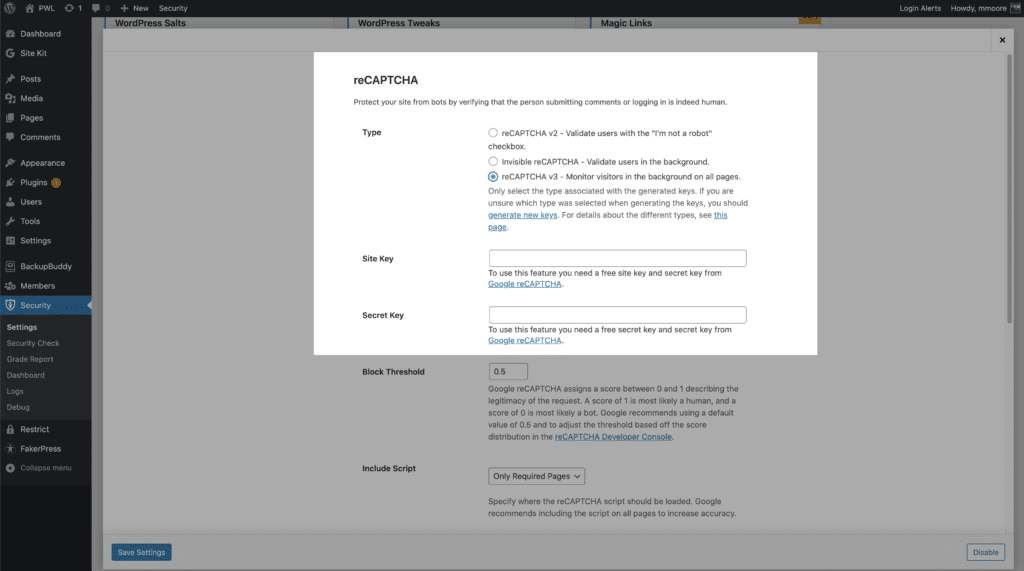
iThemes Security Pro uses the reCAPTCHA score to create a block threshold allows you to specify . Google recommends using 0.5 by default. Note that if you set the threshold too high, you may accidentally lock out legitimate users.
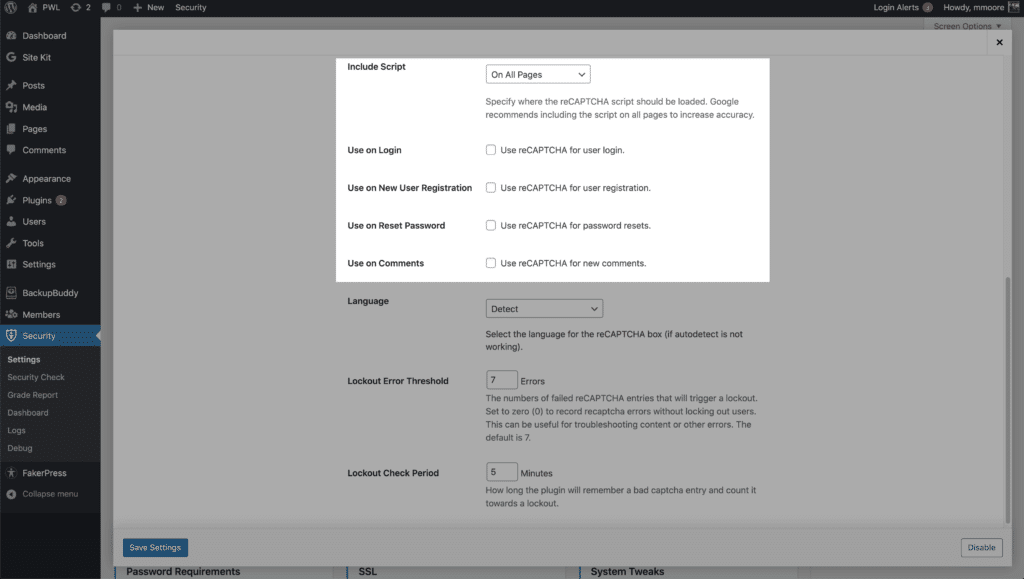
You can enable reCAPTCHA on your WordPress user registration, password reset, login and comments. iThemes Security Pro allows you to run the Google reCAPTCHA script on all pages to improve the accuracy of the bot vs human score. Enabling reCAPTCHA v3 is a great way to protect your WordPress login details.
The final step in protecting your WordPress login is to limit access to your WordPress dashboard to a range of devices. iThemes Security Pro Trusted Devices your and other users have recognized devices that they use to log in to your WordPress site. When a user logs in on an unrecognized device, Trusted Devices can restrict their admin-level capabilities. This means that a hacker can bypass your other login security methods - highly unlikely - without being able to make malicious changes to your website.
Trusted Devices to start using them, enable them on the main page of the security settings and then click Configure Settings Click on the button.