It's easy to make security mistakes in WordPress. The most common mistakes in your WordPress security can be based on outdated information, common WordPress security myths, or not knowing WordPress security best practices.
While WordPress itself is secure, avoiding WordPress security errors requires some effort from site owners. In this article, we'll cover the 10 biggest WordPress security bugs with tips on how to avoid them.
[lwptoc]
We'll cover everything from the quality of your WordPress server, to the themes and plugins you use, to your WordPress admin login.
1. Poor Hosting Selection
Not all web hosts are created equal, and choosing one on price alone could end up costing you a lot more in the long run due to WordPress security bugs.
Most shared hosting environments are secure, but some do not properly segregate user accounts. If user accounts are not properly segregated, a single compromised account can shut down every website on that shared server.
Your host should be vigilant about applying the latest security patches and following other important hosting security best practices related to server and file security.
How to Avoid Choosing Poor Hosting
Choose a reputable hosting with a solid security record for your website.
2. Not Having a WordPress Backup Plan

Backups and security don't seem to be related. But trust us, backing up your WordPress website after a ransomware attack can save your site's life.
5 Best WordPress Backup Plugins (2020) you can choose the best backup plugin by reading our article.
A ransomware attack is when a hacker encrypts your website files, making them and your website inaccessible. To regain access to your website, you need a key to decrypt the files. The hacker will be more than happy to give you the key for a hefty fee.
Backing up your WordPress website allows you to restore your website to a state before it was held for ransom. You regain access to your website without having to pay the demanded ransom.
How to Prevent No Website Backup
Set up a program to back up your website regularly. 5 Best WordPress Backup Plugins (2020)
3. Unsecured Inputs
The WordPress login is the most hacked and potentially most vulnerable part of any WordPress site. By default, WordPress does not have a plugin of its own to limit the number of failed login attempts a person can make. Without a limit on the number of failed login attempts an attacker can make, they can keep trying an infinite number of usernames and passwords until they succeed.
Your WordPress login is a lot like the front door of your house. Without a lock on your front door, it would be easy for anyone to walk right into your home, start moving your furniture, smash your stuff, and steal your TV. It makes sense to add a lock to your front door to make it harder for a would-be thief to break into your home.
Preventing an Insecure Login
Use a WordPress security plugin to limit invalid login attempts.
4. Protection Against Automated Bot Attacks
A bot is a piece of software programmed to perform a specific list of tasks. It creates a set of instructions that a bot will automatically follow without the developer having to tell it to start. Bots perform repetitive and mundane tasks much faster than we do.
Some of these bots are programmed for nefarious reasons, such as
Brute Force .
Content Scraping Boots is programmed to download your website content without your permission. The bot can replicate the content for use on the attacker's website to improve their SEO and steal your site traffic.
Spambots clutter your comments with promises of becoming a millionaire while working from home in the hopes of sending your visitors to malicious websites.
How to Avoid Automated Bot Attacks?
You can improve this WordPress security by using automated bot protection like Google reCAPTCHA on your website.
5. Using Sensitive Versions of Plugins, Themes or WordPress Core
Vulnerable WordPress plugins or themes are the biggest WordPress security mistake you can make. Keeping software up to date is an essential part of any security strategy, and this includes the WordPress core, your themes and plugins. Version updates aren't just for bug fixes and new features. Updates can also include critical security patches. Without this patch you are leaving your phone, computer, server, router or website open to attacks.
6. Weak User Security
Poor user security is a major WordPress security flaw. Simply put: A single WordPress admin user with a weak password can weaken every other website security measure you have in place. User security is therefore an essential part of any WordPress security strategy.
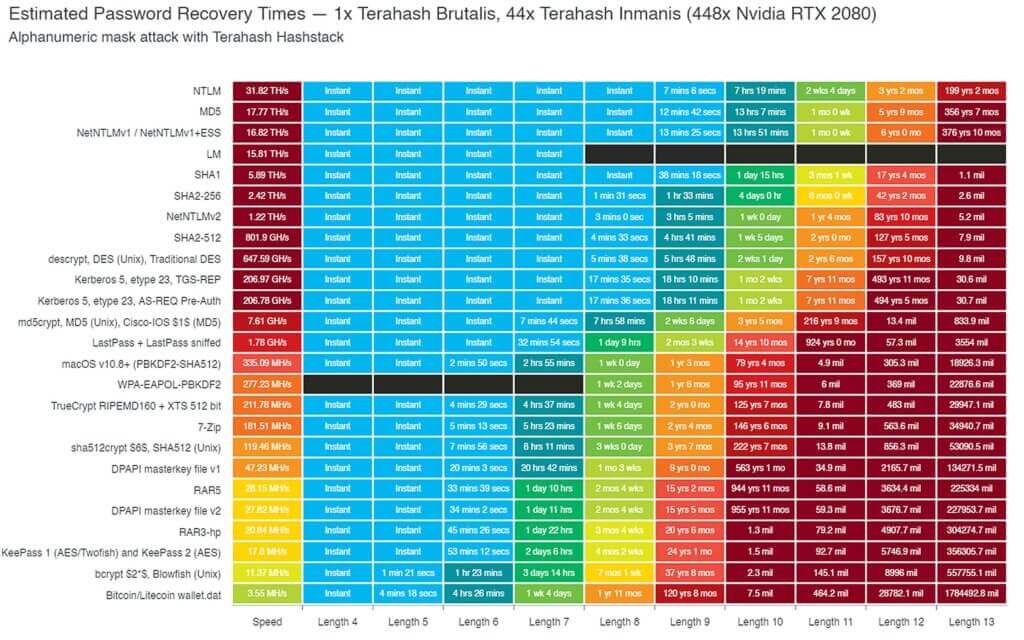
By default WordPress stored in the WP database uses MD5 to hash user passwords . So, according to this table, Terahash can crack an 8-character password almost instantly. This is not only very impressive, but also really scary.
Worse still, even though % 41 of people know that reusing passwords is a poor practice, % 59 of people still reuse their passwords everywhere!
Hackers use a form of brute force called a dictionary attack, which is attacked. A dictionary attack is a method of breaking into a WordPress website with commonly used passwords seen in database dumps.
How to Prevent Weak User Security
The best way to avoid the WordPress security bug related to weak user security is to create a strong password policy and use two-factor authentication.
Two-factor authentication is the process of verifying a person's identity by requiring two separate verification methods. Google, on his blog shared that using two-factor authentication can stop automated bot attacks% 100.
7. Unencrypted Communication (No SSL)
Not encrypting communications on your website is a serious WordPress security mistake. When we make an online purchase, communication takes place between your browser and the online store. For example, when we enter our credit card number into our browser, our browser will share the number with the online store. Once the store receives the payment, it tells your browser to notify you that your purchase was successful.
One thing to keep in mind about the information shared between our browser and the store's server is that the information makes several stops in transit. If the communication is not encrypted, a hacker could steal our credit card before reaching the final destination of the store's server.
To better understand how encryption works, consider how our purchases are delivered. If you have ever tracked the delivery status of an online purchase, you would have seen that your order made several stops before it arrived at your home. If the seller didn't package your purchase correctly, it would have been easy for people to see your purchase.
How to Avoid Unencrypted Communication
You will need an SSL certificate to encrypt communication on your website. If your WordPress website does not have SSL, the first thing you should do is to ask your hosting provider if they provide a free SSL certificate and configuration.
Cloudflare, WordPress websites a free shared SSL certificate for offers . With a shared SSL certificate not to be if you prefer, and from the command line if you are satisfied , CertBot is an excellent option. Certbot is Let's only for you Encrypt not only generates a free SSL certificate for you, but also automatically manages its renewal for you.
8. Inadequate Safety Recording and Monitoring
Inadequate login on your website, OWASP web application security risks to the top 10 logging is a big enough WordPress security bug. Logging is an essential part of your WordPress security strategy. Tracking the right behavior helps you identify and stop attacks, detect a breach, and access and repair the damage done to your website after a successful attack.
Inadequate logging and monitoring can cause a delay in detecting a security breach. Most breach investigations show that the time to detect a breach is more than 200 days! This time allows an attacker to breach other systems, modify, steal or destroy more data.
Inadequate Logging
Add security logging to your website to avoid this WordPress security bug. You can use the tools that WordPress provides to create a logging system developer functions and filters but the easiest way to start a security log is to install a WordPress security plugin.
9. Unused Plugins and Themes
Having unused or inactive plugins and themes on your website is a major WordPress security mistake. Every piece of code on your website is a potential entry point for a hacker.
It is common practice for developers to use third-party code such as JS libraries in their plugins and themes. Unfortunately, if libraries are not properly protected, they can create vulnerabilities that attackers can exploit to hack your website.
How to Avoid Plugins and Themes
Remove unnecessary plugins and themes on your WordPress site and delete them completely to limit the number of access points and executable code on your website.
Additionally, avoid using abandoned WordPress plugins. If any plugin installed on your WordPress site hasn't received an update in six months or more.
10. Installing Software from Untrusted Sources
Installing software from untrusted sources is one of the fastest ways to create a WordPress security bug. You should be wary of the "invalid" version of commercial plugins. Often, these free or heavily discounted versions of professional plugins contain malicious code.
If you're the one who installed malware, it doesn't matter how you locked down your WordPress site.
How to Avoid Software from Untrusted Sources
You should only install software you get from WordPress.org, well-known commercial repositories or directly from reputable developers.
If the WordPress plugin or theme is not distributed on the developer's website, you'll want to do your due diligence before downloading the plugin. Reach out to the developers to see if they are in any way affiliated with the website offering their product for free or at a discounted price.
Summary Explaining the 10 Biggest WordPress Security Bugs
As we can see, there are many potential WordPress security bugs. Fortunately, all security bugs can be easily avoided with a little effort from us.
A Simple WordPress Security Checklist
Most WordPress vulnerabilities can be mitigated by taking a proactive approach to WordPress security. To summarize, here is a simple WordPress security checklist to follow:
- 1. Choose quality hosting.
- 2. Create a backup plan.
- 3. Limit invalid login attempts
- 4. Add automatic bot protection.
- 5. Avoid using vulnerable software.
- 6. Use strong passwords and 2fa.
- 7. Encrypt communication with SSL.
- 8. Add a WordPress security log.
- 9. Remove unused plugins and themes.
- 10. Install software only from trusted sources.
In a list compiled by Splash Data, the most common password found in all data dumps was 123456. Data dump, somewhere on the internet thrown is a hacked database full of user passwords. If the most common password in the data dumps is 123456, can you imagine how many people on your website use a weak password?
Hacker's tools are getting better and they can bypass passwords faster than ever before. For example, a high-performance password cracking company Terahash created by the company "The Hashstack of the RTX 2080s". Their graph shows how long it takes to crack a password using a hashstack set of 448x RTX 2080s.
Hackers target patched vulnerabilities (including plugins and themes on your website) because they know users don't update them. It is an industry standard to publicly disclose vulnerabilities the day they are patched. Once a vulnerability is publicly disclosed, it becomes a "known vulnerability" for outdated and unpatched versions of software. Software with known vulnerabilities is an easy target for hackers.
Hackers like easy targets. Having outdated software with known vulnerabilities is like giving a hacker step-by-step instructions to break into your WordPress website.
Having a vulnerable plugin or theme where a patch is available but not applied is the number one culprit of hacked WordPress websites.
How to Avoid Using Vulnerable Plugins and Themes
Keep all your plugins and themes up to date to prevent vulnerable software from exploiting WordPress security flaws.